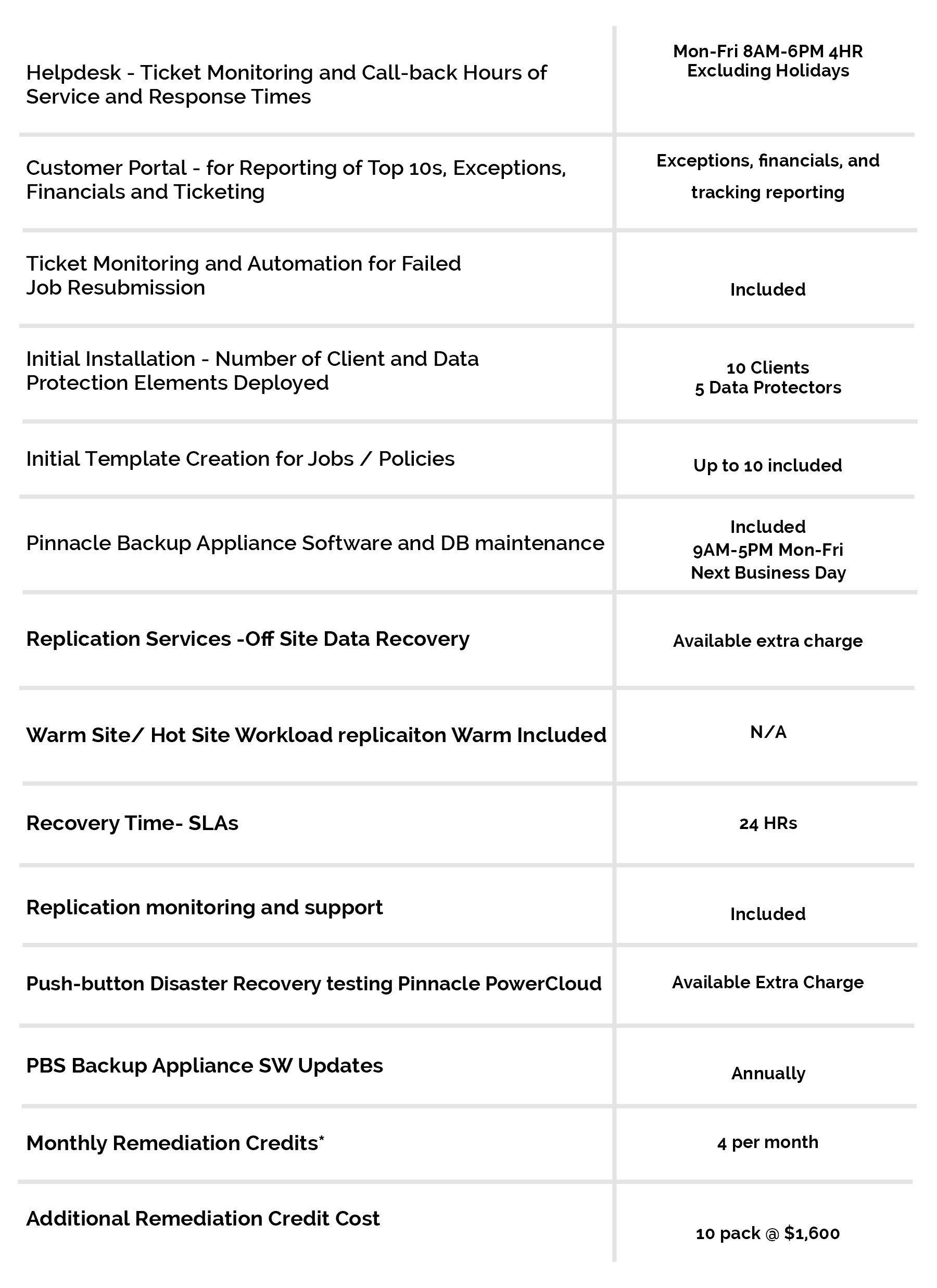
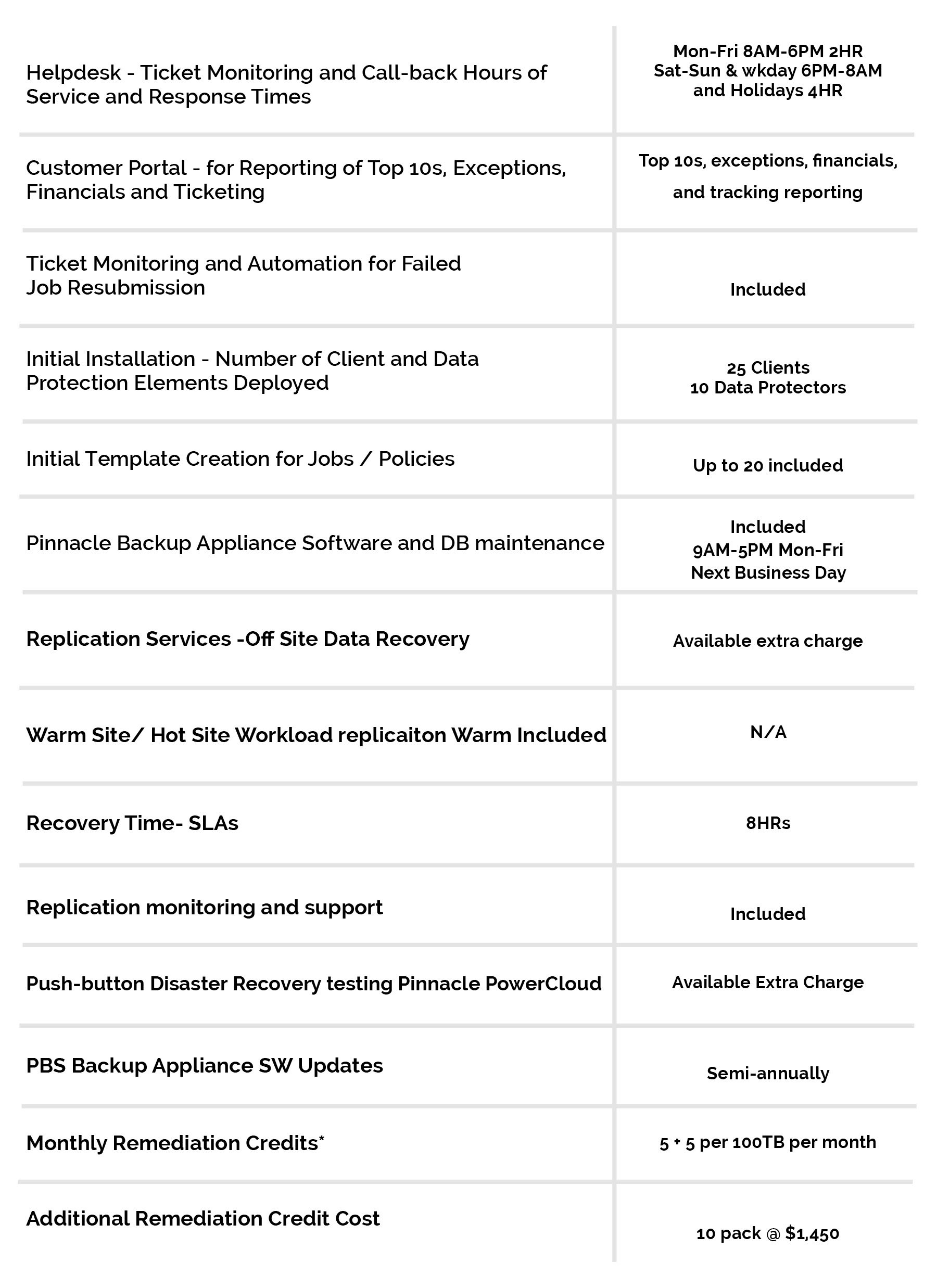
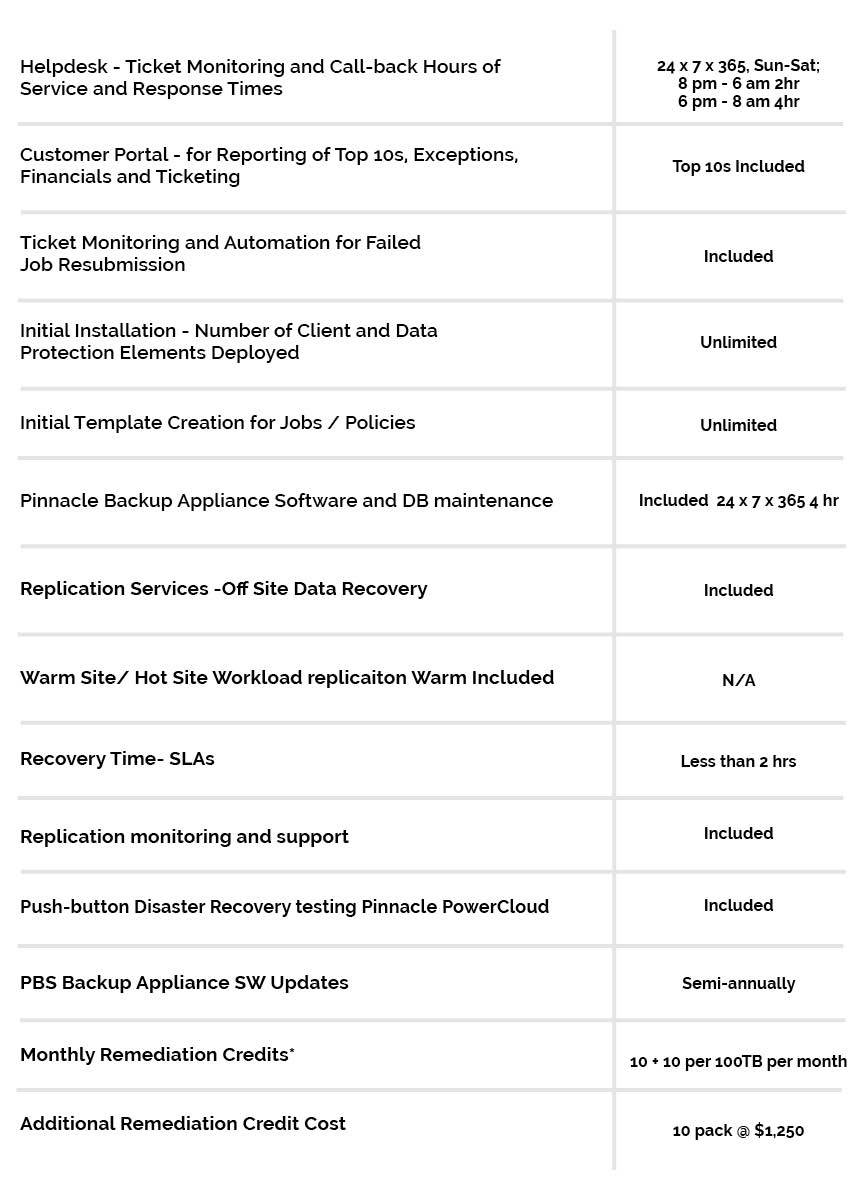
03 Apr Information Security Part 3: Network/Transport Layer Security
Things you can do today to secure your network
In part three of our information security series, Alan Bunyard, Solutions Architect for Pinnacle shares how you can improve your network and transport layer security through L3 switches, routers, and traditional stateful firewalls.
Securing your network at L3/L4 becomes a bit harder when following our Information Security Network/Transport layer security theme of making the best of what you have today. The scope of network equipment is much larger than the primary L2 network switches that was the focus of the previous sections. Part 3 of the Information Security series addresses L3 switches, routers, and traditional stateful firewalls. This doesn’t even consider the many “next gen” variants of those devices or virtually unlimited number of specialty devices like load balancers, stand-alone IPS systems, network access control, etc. We are limiting the scope of this conversation to those traditional network devices that are ubiquitous in all production networks. These are the lowest hanging fruit for all entities, especially SMB’s seeking to secure their networks before they are able to purchase the newer security technologies.
Flat networks
This isn’t just a mom and pop operation problem, you would be surprised how often we discover flat networks at large organizations. Often times what we see is that the network engineer in 1998 setup a network with a 16-bit subnet mask with 65,536 usable IP addresses which is enough IP space to last for 200 years for the common SMB. And it did last! But as the network grew larger and more sophisticated, it became harder to segment for security because so many services were running in that flat network. Moving production services can be a lot of work when production email servers, databases, and applications all running in the same subnet and VLAN as wired and wireless users today. Sometimes even guest networks are dumped into the corporate VLAN. Networks get stuck with these bad designs that were started decades ago before switches even supported VLANs and networks were still running cheap network hubs. It’s time to segment the network into new subnets and VLANs. This can be accomplished on your L3 switch, router, or firewall as appropriate for the size of your organization and its current equipment. The work to move production services into the newly segment network is truly the hard part that discourages many from even starting. Once segmented, VLAN’s alone won’t secure the datacenter and sensitive networks. Your L3 device will freely pass packets between those new networks just as your L2 switches once passed packets directly between client and server. This is where access list can help – to a point.
ACLs – Stateless
Your L3 switches and routers typically don’t support stateful inspection but they can create ACLs and fake stateful behaviors on return traffic by using the “TCP established” access control entry. This could allow a client to contact a server on port 80 and allow the TCP return traffic dynamically. Start by creating the access list as close to the protected network as possible. On the SVI or router interface that supports L3 for the protected network (e.g server vlan), create and apply inbound and outbound ACL. If possible, start with a least privilege mindset and open it up with only the required individual IPs, networks, and source/destination ports. For a small organization or a branch office, this is easily managed. If you have 1000’s of ACL entries and continue to grow, it’s probably time to look at something more advanced than stateless ACL’s or you’ll have a tough time managing the rules.
ACLs – Stateful Inspection
Most SMB’s put a stateful firewall at their Internet Edge. If you can place a stateful firewall between your users and critical networks, that’s even better. You can even use the same physical firewall if it has the capacity to handle the extra work. All the same concepts mentioned for stateless rules apply, but you are using a firewall capable of stateful inspection. It makes creating rules easier! More can be accomplished using fewer lines of configuration and most firewalls can even create a stateful connection for return UDP traffic even if the return UDP traffic is on a different port and was requested via TCP by the client. Something those stateless ACL’s couldn’t do dynamically. Creating the rules in the firewall is easy but planning them can take time. Start with a list of applications being accessed in the protected network and start researching the requirements on the software manufacturer’s sites, they usually provide all necessary documentation for firewall policy creation.
Combine your ACL’s with private VLAN’s (PVLANS)
It’s a manual process, but it accomplishes micro-segmentation that would normally require modern software networking overlays. It won’t scale well for large enterprises, but if you’re an SMB with a mostly static environment this is an easy win!
Get a next generation firewall with centralized management
All of this is a lot of work. It can be simplified by getting a next generation firewall with centralized management.
Look for Part 4 of our Information Security: Things You Can Do Today to Secure Your Network series coming in a few weeks! It will focus on Application Layer Security. For more information on how to protect your network and full-scale solutions offerings that we have available, get in touch with us today!
Writer: Alan Bunyard, solutions architect at Pinnacle Business Systems

Information Security 4-part Series
- Information Security Part 1: Physical Layer Security
- Information Security Part 2: Datalink Layer Security
- Information Security Part 3: Network/Transport Layer Security
- Information Security Part 4: Application Layer Security